Building "data sovereignty" system as a neutral cloud provider:
Customer data is not disclosed to third parties
Three stage data cancellation (logic zeroing = > physical demagnetization = medium pulverization)
Establish data inheritance mechanism and support key management entrusted and directed transfer
Innovations with block chaining techniques:
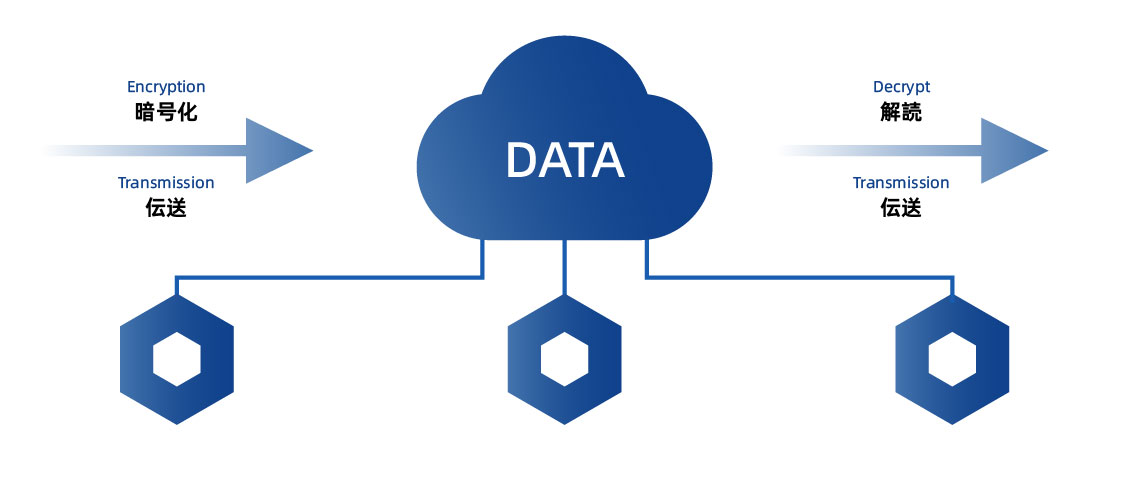
Data encryption fragment distributed with geographical distribution
Smart dynamic replica control
Quantum protection signature algorithm for metadata protection
TEE(Trusted Execution Environment) Building on base
1. CPU Instruction set level isolation
2. TensorFlow/PyTorch Ensuring equal framework compatibility
3. Realization of "invisible visibility" in association learning + confidential computation
4. AI Zero knowledge proof verification function in model inference process
Next generation encryption transport system
Dual defense of next generation encryption systems
Transfer layer: TLS1.3+ Post quantum crypto hybrid
App layer: dynamic searchable Cryptography (DSE) technology
Control layer: Zero segmentation based microsegmentation
Audit layer: domestic traffic fingerprint preservation of all traffic
Epoch-making AI Collaborative security framework
1. Differential privacy data expansion
2. Parameter aggregation platform
3. Cross cloud secure box environment
Data procurement visualization tracking system